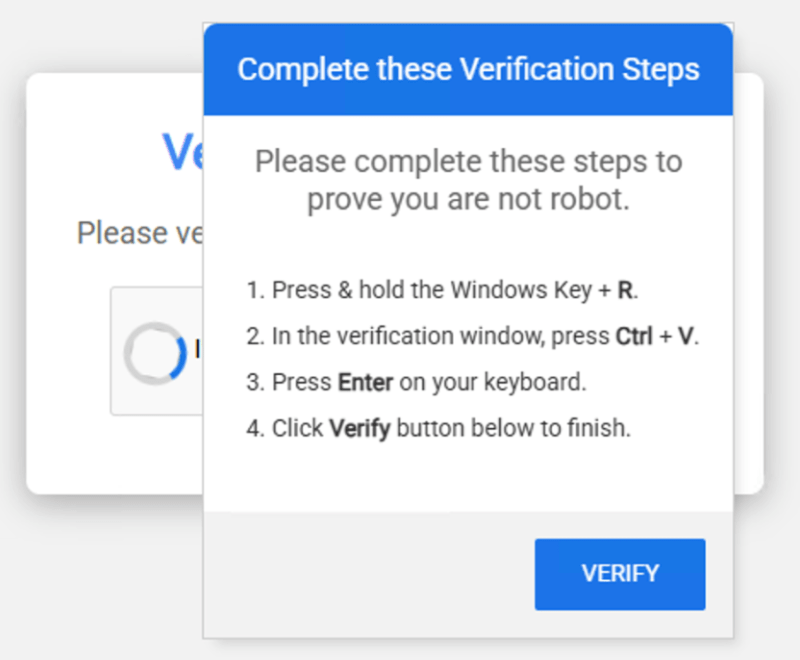
In the ever-evolving world of cybersecurity, attackers are always developing new ways to trick unsuspecting victims. While we’ve shared the dangers of Windows Update pop-ups, attackers have started evolving this scam to include other computer fixes or updates. What makes this scam particularly dangerous is that it doesn’t rely on tricking users into downloading and running suspicious files. Instead, the attacker manipulates the user into executing the commands themselves, effectively handing control to the attacker without realizing it.
How the “Fix or Update” Scam Works
 |
 |
The malicious websites typically display a button, link, or message urging the victim to verify, fix an error or update something that’s broken. In reality, the action triggers the malicious command. Examples include:
- A fake CAPTCHA or “I’m not a robot” page that asks for verification
- A Cloudflare-style verification screen
- A fake Microsoft Word error message
- A phony Discord invite page
- Malvertising with a fake warning message
Instead of prompting a file download, the page instructs the user to take an action. Like the examples above, it usually asks the user to press Windows + R to open the Run box and pasting in a command. That command downloads and executes a malicious script from the internet, infecting the user’s system.
Hackers will usually hide the command with harmless-looking text to make it appear less suspicious. Other variations include asking the victim to paste a command into the Command Prompt or abusing built-in Windows protocols to run commands directly from the browser.
What Happens After Running the Command

Once executed, the malicious command typically:
- Downloads a script that installs the actual malware payload
- Steals sensitive information such as login credentials, financial details, or cryptocurrency wallets
- Installs persistence (for example, a scheduled task) so the malware reinstalls itself even if the user deletes some files
In short, the victim’s system is compromised, and removing the infection can be extremely difficult.
The malicious websites typically display a button, link, or message urging the victim to “fix” an error or “update” something that’s broken. In reality, the action triggers the malicious command.
Variations of the Pop Up Scams

While this technique is most often seen on Windows systems, attackers are also targeting macOS and other platforms. On a Mac, the victim may be tricked into running a terminal command that prompts for their password. Once entered, the attacker can bypass built-in security controls and download malware. This cross-platform approach highlights how attackers adapt their techniques to reach the broadest possible audience.
As awareness spreads about these types of pop up scams, some variations are starting to, well, pop up. These include:
- Using the Command Prompt instead of the Run box
- Exploiting Windows protocols (like
ms-calculatororms-clock) to run hidden commands - Abusing Windows Explorer by creating malicious shortcut files that launch commands when opened
Each method is designed to make the victim feel like they’re taking a harmless action—when in reality, they’re installing malware.
How to Protect Yourself from these Pop Up Scams

The good news: this scam requires user interaction. So awareness and caution can go a long way to preventing people from doing what the hackers want. Here are a few key defenses:
- Never paste commands from a website into Run, Command Prompt, or Terminal. Legitimate sites won’t ask you to do this.
- Be skeptical of instructions to fix problems outside the browser. That’s a classic red flag.
- Check pop-ups carefully. If your browser asks to open another app, pause before accepting—it could be a trick.
- Keep your operating system and apps updated. Patches help protect against vulnerabilities that attackers might exploit.
- Use strong security software. Comprehensive tools can detect and block malicious scripts, suspicious commands, and unusual system behavior.
Why the Pop UP Scam Is Growing

Traditional malware often relied on tricking people into downloading files. These pop-up scams are harder to spot because they disguises itself as a validation or troubleshooting step, reaching a wider group of victims who aren’t even searching for files. As online verification steps (like CAPTCHAs) become more familiar, users are more likely to trust them. That false sense of legitimacy is exactly what attackers exploit.
These pop up scams are a reminder that not all threats come from obvious downloads or email attachments. Sometimes, the danger comes when you’re convinced to take the action yourself. By staying cautious, refusing to run commands from untrusted websites, and keeping your devices secure, you can avoid falling victim to this deceptive new scam. If a website tells you to “verify,” “fix,” or “update” something by running a command outside your browser, it’s not a fix, it’s a trap.